Security Risks in Logistics APIs Used by E-Commerce Platforms

Our research examines the security flaws that we found in the logistics API implementation of e-commerce platforms that can potentially expose the consumers’ personal information. We discuss the security risks that such flaws present for software engineers, e-commerce platform providers, and consumers.
September 20, 2022
Read time: ( words)
The connectivity that we’ve experienced of late has improved at an unprecedented speed and scale largely because application programming interfaces (APIs) enable the seamless integration of different systems from different entities. APIs integrate data and services between businesses and third-party vendors to address various market needs, enhance the provision of services, and obtain consumer insights, thus driving the significant growth of e-commerce in recent years.
If API integration is improperly implemented, the risk of leaking personally identifiable information (PII) could arise. Many verticals that use API communication should be sufficiently secured especially when sensitive data is being transmitted. Otherwise, inadvertent PII leakage can lead to serious consequences not only for organizations that fail to fulfill their legal or compliance obligations but also for consumers whose PII is exposed. Our research paper, “Examining Security Risks in Logistics APIs Used by Online Shopping Platforms,” looks more closely at e-commerce and logistics, two markets that have significantly expanded during the pandemic.
The e-commerce segment showed steady growth even before the pandemic happened, but Covid-19 gave it a forceful push as everyone tried to work around movement restrictions to comply with government-imposed lockdowns. This resulted in a massive shift to e-commerce platforms to access goods and services, so the surge in demand exerted pressure on online merchants to ensure the timeliness of deliveries.
External logistics providers address the merchants’ logistical needs by managing this aspect of the supply chain process, which is done either partially or through a complete logistics solution. It can be a simple courier service that merchants use to deliver products (a second-party logistics or 2PL), or a third-party logistics (3PL) service comprised of warehousing, fulfillment, and delivery of products. Figure 1 (retrieved here) shows how an external logistics provider works in different use cases.
Initially, we investigated 3PL and 4PL providers that were unwittingly exposing PII through unsecure methods. However, as the research progressed, we also discovered that, aside from 3PL and 4PL providers that leave sensitive information exposed, services that were already integrated into their systems also had security vulnerabilities of their own, thus compounding the risks for the entire e-commerce ecosystem. E-commerce platforms allow merchants to integrate existing external logistics providers through APIs to consolidate different services into one platform. API keys and authentication keys that e-commerce platforms and logistics providers share are supposedly meant to facilitate a secure channel for communication.
There are many ways that PII is exposed from logistics API implementation that are related to unsecure coding practices. We discuss some of them in the following section.
URL query parameters
One of the coding practices that inadvertently exposes PII involves URL query parameters in e-commerce platforms and logistics APIs. E-commerce platforms usually require customers to log in to an account or choose a guest checkout option. Some online shopping websites use unique URLs that they send to the users through email or SMS which redirects them to the website where the order information can be accessed.
The presumption that the combined use of a unique URL sent to an email address or phone number owned by the recipient sufficiently protects PII is problematic as this engenders a false sense of security. Our study shows that unauthorized parties can still retrieve a customer’s PII by directly accessing a URL without the need for further authentication.
Authentication keys in URL parameters
When consumers place an order in an online store, the store sends them a confirmation email with a URL link and the authentication key on the URL parameter to view the order details. This key is used to verify if the user checking the order page is the recipient of the email. The order page contains information such as the customer’s name, email address, phone number, and payment method.
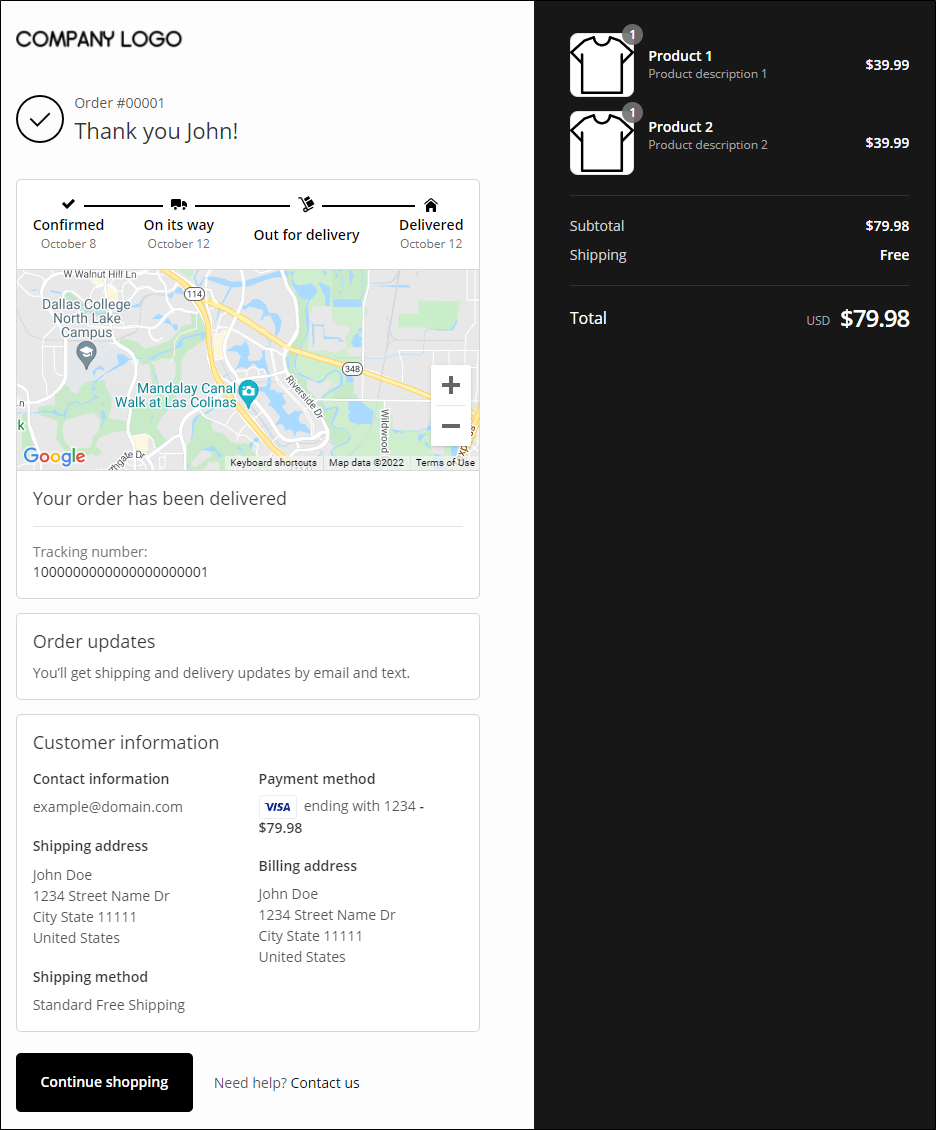
The practice of passing authentication keys as part of the URL parameter can leak PII given that such keys can still be retrieved using other means such as accessing the user’s browsing history and router logs. The use of unencrypted URL query parameters makes the PII susceptible to sniffing and man-in-the-middle attacks.
Unauthenticated 3PL APIs
While the basic components of a 3PL service that online retailers use include processing of orders, shipping, and tracking, we also found a 3PL provider’s API (referred to as Company X on Figure 3) disclosing PII through an unauthenticated API service. This API service is being used by four other 3PL providers to display customers’ order information.
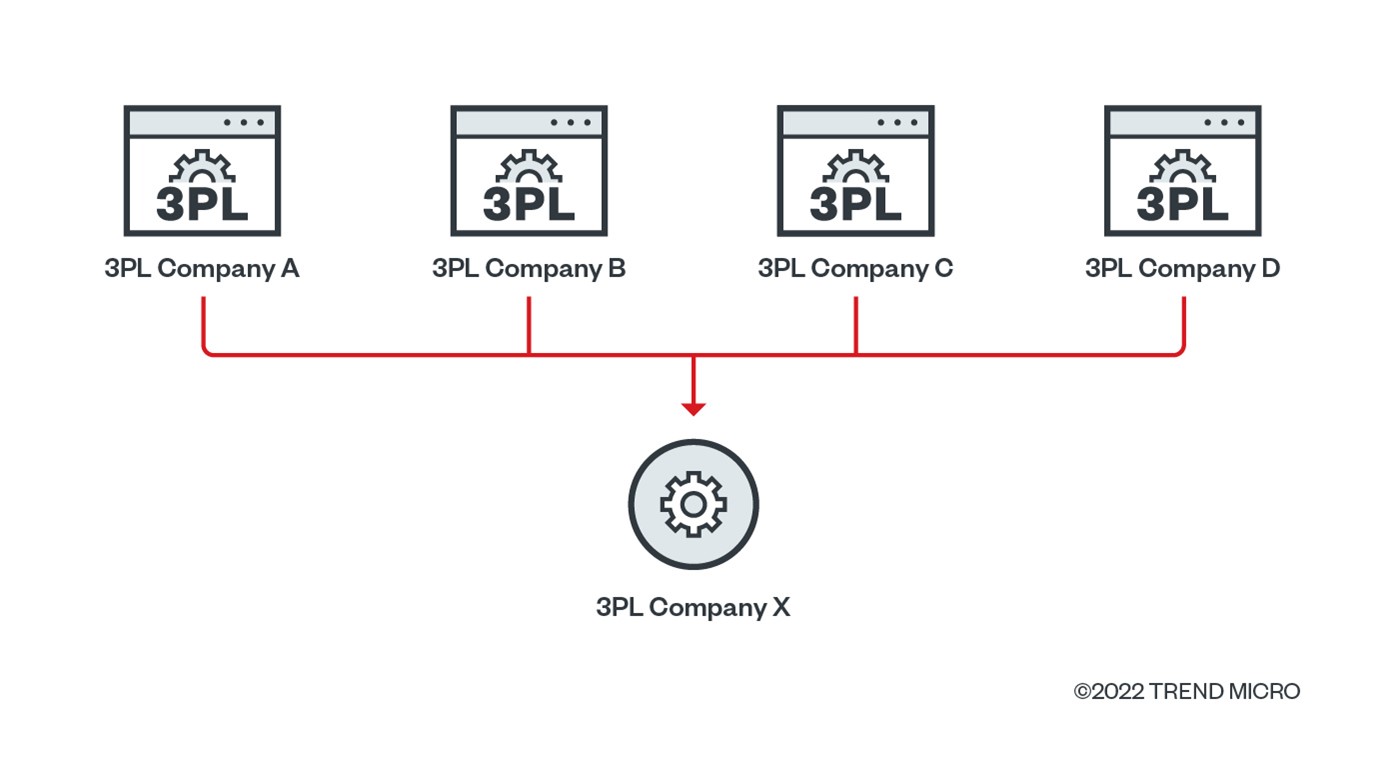
When we inspected the order information page through the URL link provided by one of the four 3PL providers and checked the HTTP request made to view the order details, we discovered that the page we were viewing was making an HTTP request in the background to another 3PL provider to obtain the order details.
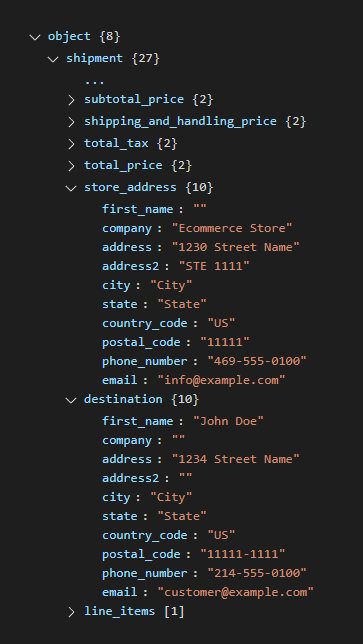
We scrutinized the URL parameters of the URL for the order information page. One of the API requests made in the background used an unauthenticated method to verify API requests, which returned a full set of information about the customer and the purchased items. Therefore, anyone who has access to the order information URL can reconstruct the URL to retrieve a customer’s PII.
Sessions and cookies with expiration set beyond the recommended duration
Another unsecure coding practice is the use of session and cookies with improperly set expiration dates by some 3PL providers. We observed many instances of noncompliance by 3PL providers with the best security practices specific to the use of sessions and cookies to regulate authentication. This method is one of the best practices that the Open Web Application Security Project’s (OWASP) has recommended, although session time to live (TTL) should always expire as soon as the transaction is completed or right after the user quits the connection. Malicious actors can use the detected cookie key to replay transactions and obtain PII, which they can exploit to launch malicious schemes.
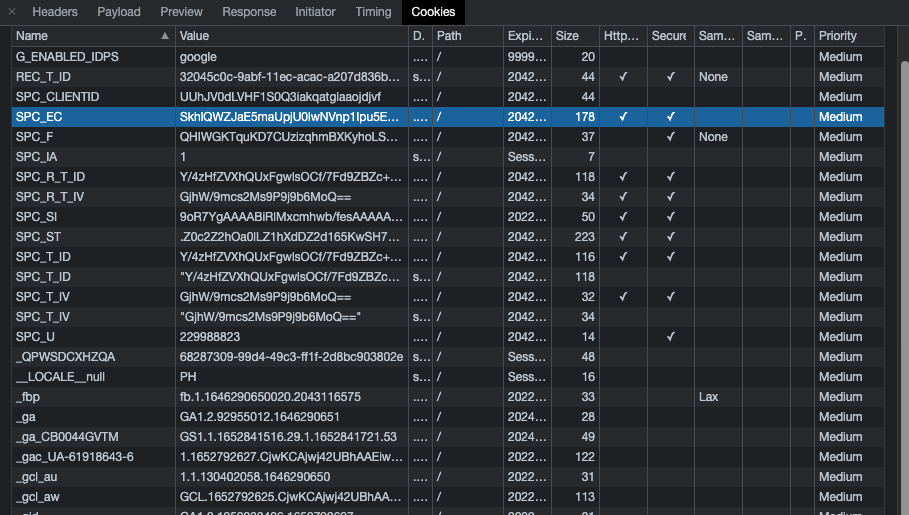
The lure of leaked PII, its potential use for malevolent purposes, and the crucial role that APIs play in e-commerce strongly justify the need for stakeholders to adopt a deliberate approach to ensure the security of logistics API implementation.
The following are some of the recommendations provided in our research paper on how coding practices can be improved.
1. Session and cookie expiration
Session expiration determines when to terminate a session’s authenticated connection to the server. By default, it is set to one day or the session is terminated after users cease their connection to the site. The same mechanism applies to cookie expiration. Session timeout should be activated once the user is no longer performing any action on the website to prevent expired cookies from being reused.
2. Excessive data exposure
Excessive data exposure happens when data beyond what the transaction requires is exposed. Some developer implementations send all the information of a transaction rather than what is just needed to complete a transaction. This creates a situation in which data is exposed to accounts with access restrictions or limited privileges. Leaked data from logistics API can be used for scams or fraud.
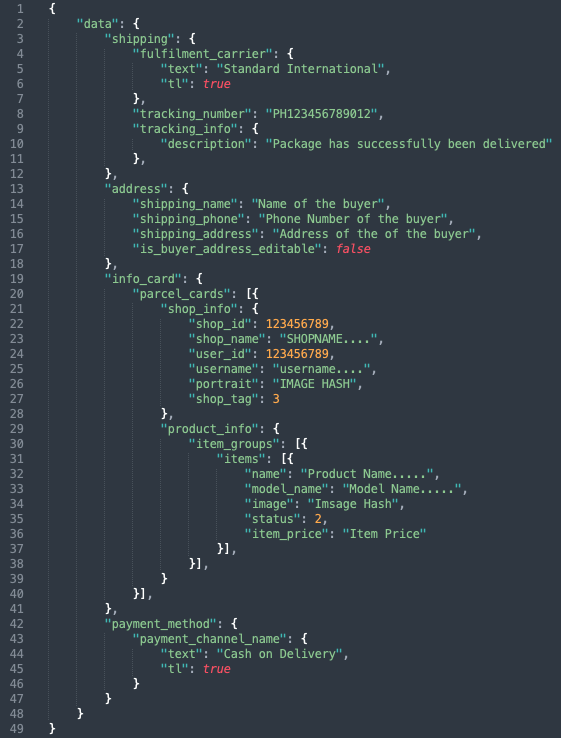
Developers should adopt the practice of discerning essential customer information needed for a transaction and classifying its risk level.
3. Broken Object Level Authorization
Typically implemented at the coding stage, object level authorization is an access control strategy done to ensure that only authorized users gain access to objects. Object level authorization checks should be implemented in every API endpoint that receives an object’s ID and performs any type of operation on the object. The tests ensure that the logged-in user has permission to perform the operation on the requested object.
A more secure practice when handling PII is to encrypt the data and require user authentication before granting access. When using 3PL API Integration, PII should be adequately protected when sharing it with 3PL-affiliated suppliers. There are many different authentication algorithms that can be used to safeguard API transactions. Tokens such as JSON Web Token (JWT) or custom tokens generated using base64 encoded with salt are essential to secure API calls.
In sum, developers should bear in mind what data should be given throughout the transaction and what authentication measures should be in place.
Consumers play an equally important role in minimizing the risk of PII exposure. The following security practices can help them keep their PII safe:
- Properly discard delivery packaging and make sure that the labels with PII are shredded or obfuscated so malicious actors can no longer read them.
- Delete browsing history especially on public or shared devices.
- Avoid the installation of unknown browser extensions to web browsers that can read and collect unencrypted URL query strings.
- Use legitimate virtual private networks (VPNs) when on public Wi-Fi networks to reduce the exposure of personal data.
- Implement two-factor or multi-factor authentication for e-commerce platforms and other sites that require users to input PII.
While business owners do not exercise direct control over the security implementation of the e-commerce platforms and logistics services that they choose, the security flaws we identified need to be tackled early on to thrive. Therefore, businesses that seek long-term success should take it upon themselves to ensure that API services are consistently and thoroughly audited, and developers of e-commerce platforms and logistics providers adopt industry best practices.
Tags
sXpIBdPeKzI9PC2p0SWMpUSM2NSxWzPyXTMLlbXmYa0R20xk

